Sensitive Compartmented Information Facility
SCIF Secure Repository
Modular and Portable construction for high security electronic information that is processed, discussed, and/or stored. Government work and government-related contract work require a SCIF.
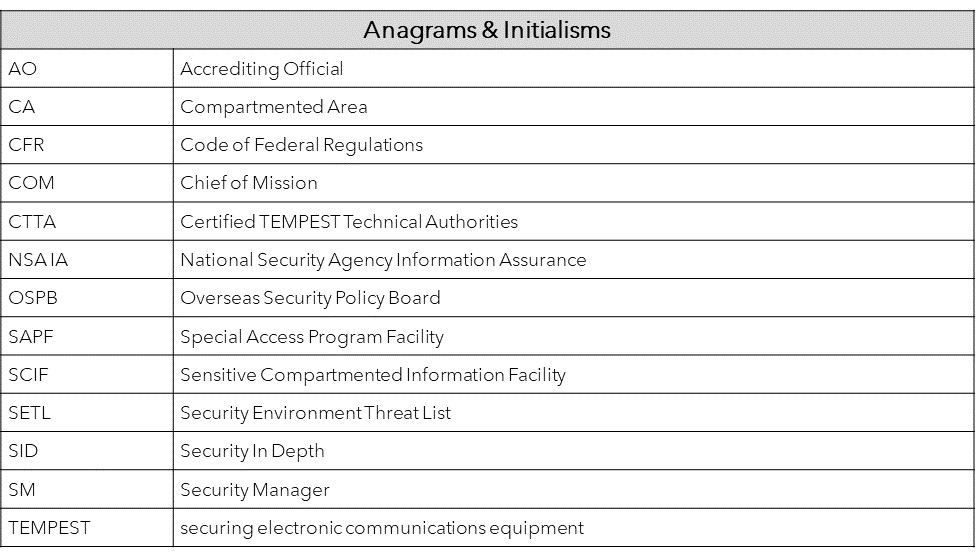
All SCIFs require specialized construction and security measures (including electronic and TEMPEST security). Every SCIF is designed and constructed according to the purpose of the facility and location. Thus, no two SCIFs are the same in construction and security measures. SCIF planning and design begins with a sponsorship by an Accrediting Official (AO) to ensure security oversight and quality control throughout development.
Design & Build Supplier, Distributor & Manufacturer
ICD 705, ICS 705-1, and ICS 705-2 Compliant Requirements
Individual physical and technical SCIF requirements are assessed by an AO and a construction Site Security Manager (SSM). Both the AO and SSM will take the customer’s needs, purpose of the facility, location, and environmental factors into consideration when designing and in the management of the construction of a SCIF.
Consult, Plans and Planning of Features of Buildings, Containers and Security
Specialists in Access Control for Accredited SCIFs
For the Operation checklist of Management of a SCIF, refer to this guide for security and data protection.
Note: The features listed below will vary depending on the risk assessments done by your AO and SSM.
- Perimeter
- Radio Frequency (RF) protection by a Certified TEMPEST Technical Authority (CTTA)
- Depending on design, walls may include TEMPEST countermeasures
- Acoustic and physical protection from outside security threats
- Access Control Systems (ACS)
- Intrusion Detection Systems (IDS)
- Compartmented areas (CA) that provide separation between control systems, compartments, and workstations. Some features of a CA include:
- Closed Storage – for storage when information is not in use
- Open Storage – access controlled storage
- SWA (Secure Working Areas) – used in discussing, handling, and/or processing secure information
- TSWA (Temporary Secure Working Areas) – for temporary use of discussing, handling, and/or processing secure information
- Interior vaults and security doors for access control
- Emergency exists and notification systems
Note: SCIFs outside the United States including Temporary, Airborne, and Shipboard SCIFs , vessel and maritime have more detailed requirements in addition to the features listed above. Those requirements can be found in Technical Specifications for Construction and Management of Sensitive Compartmented Information Facilities.
Does your facility require a SCIF? KL Security offers SCIF Container Solutions with panelized modular systems for scalable modular, portable, & mobile requirements. We assist in the acquisition of modular facilities for DoD & Government Access Control and ICD705 SCIFs or SAPF facilities. We also assist with special access control planning and commercial business security.
Call 866-867-0306 or email [email protected] to see how the experts at KL Security can assist your facility in security needs.
Technical Specifications for Construction and Management of Sensitive Compartmented Information Facilities
SCIF Container Series | Part 1: Site Evaluation

Information has been gathered from sources deemed reliable but not guaranteed and is subject to change without notice. The information contained in this site is provided for informational purposes only.