By: Colene King
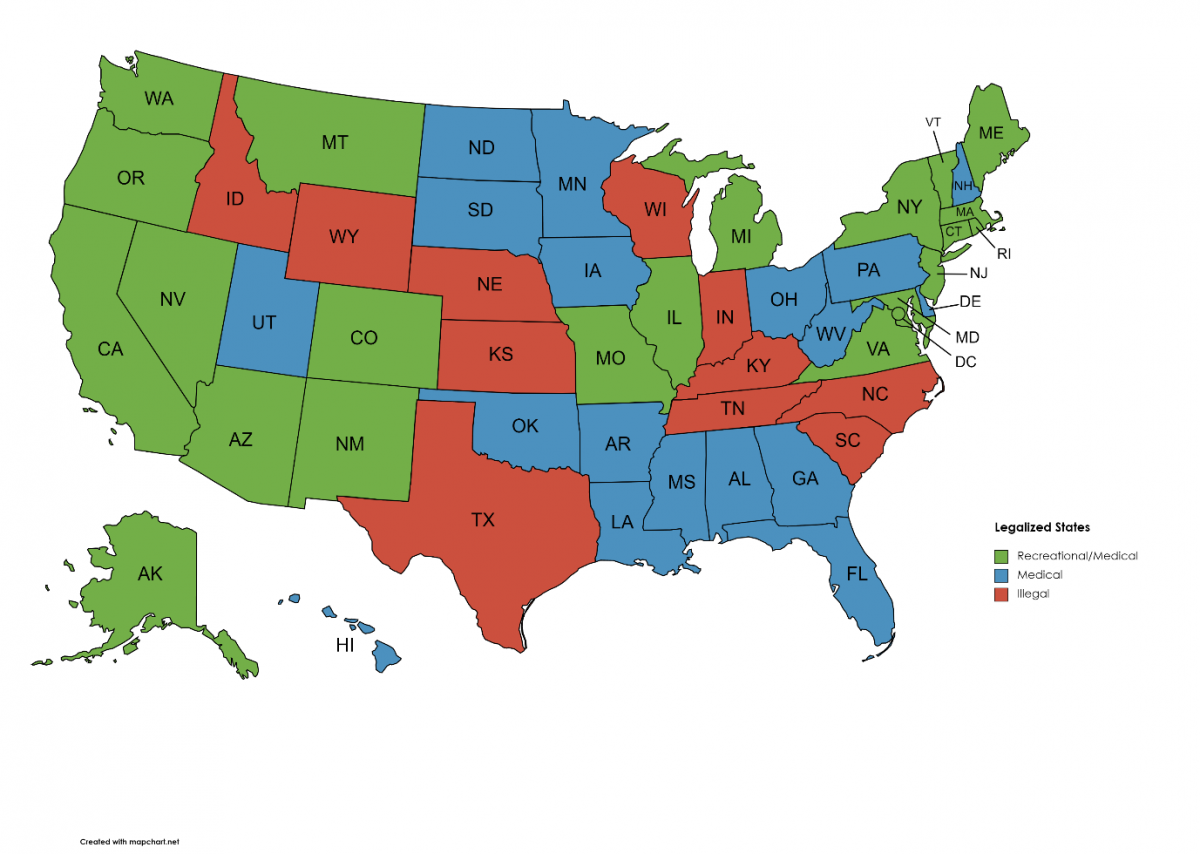
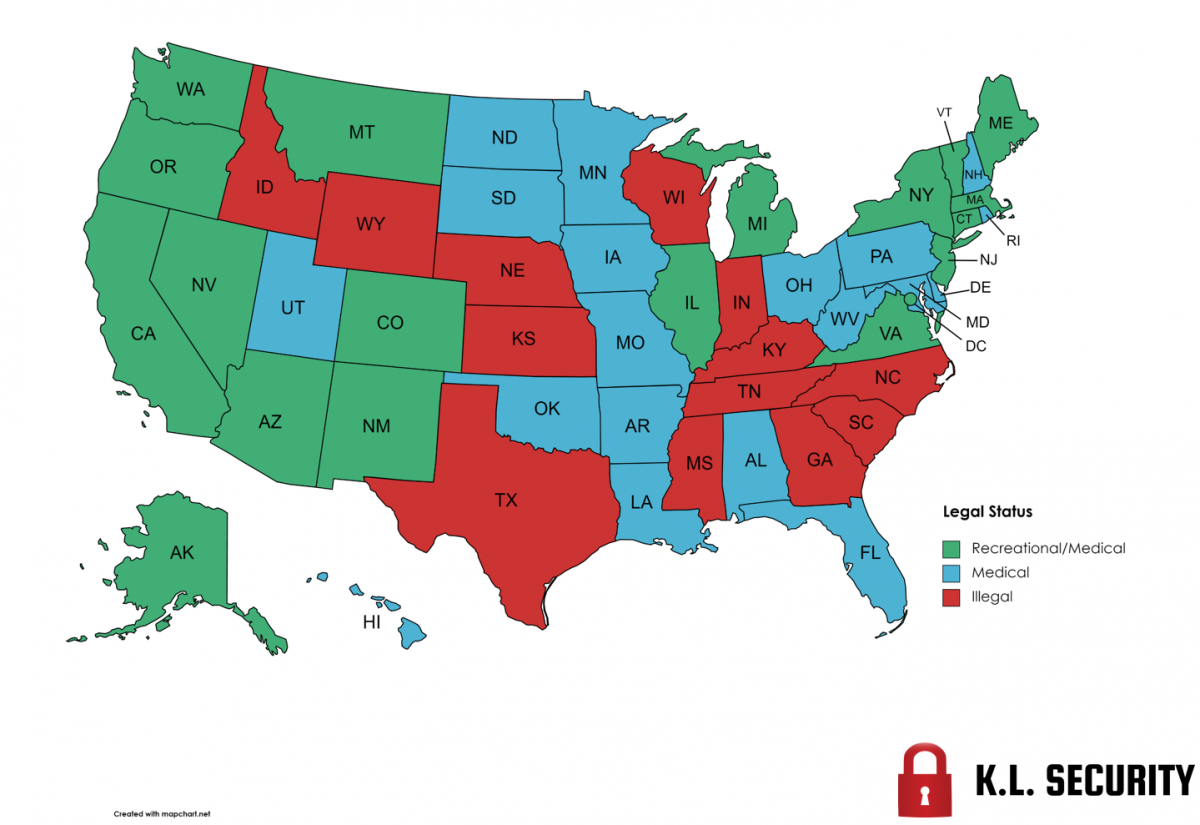
2022 has been another banner year for the ongoing fight to end marijuana prohibition in the United States. The list of legal states just keeps growing, with three states joining in on the movement this year. Rhode Island started off the year with signing the legislation to legalize the personal use and sale of marijuana to adults 21 and over. Then, last month’s primary election welcomed the two newest states to legalize the adult-use of marijuana for 21 and over. On November 8th voters in Arkansas, Maryland, Missouri, North Dakota, and South Dakota took to the polls to decide on their state’s future of legal cannabis for adults. Of the 5 states, 2 of them passed the initiative! We would like to congratulate the residents of Rhode Island, Maryland, and Missouri on becoming the 19th , 20th , and 21st states to legalize adult-use marijuana in the US. 2022 has shown great progress for our country’s future of legal marijuana for all Americans.
Rhode Island kicked off the year with signing the legalization legislation in May, seeing their first adult-use cannabis sales on December 1st. Nearly 85% of the municipalities in the small state opted in for legal sales, one of the highest in the country. ‘The Ocean State’ is projected to see $80 million in sales within the first year and $300 million by their fourth year. (Casacchia, 2022)
Maryland passed the referendum with 66% of voters in support of legalization. Voters were asked a simple question on their November 8th ballot “Do you favor the legalization of the use of cannabis by an individual who is at least 21 years of age on or after July 1st, 2023, in the state of Maryland?” (Jaeger, 2022) Beginning July 1st of 2023, Marylanders who are 21 and over will legally be able to consume, possess, and grow marijuana. The state is projected to generate as much as $600 million in its first year as a legal market and possibly reaching $1 billion by its fourth year. (Roberts, 2022)
In Missouri, the bill passed with a much closer margin, 53% to 47% in favor of legalization. This makes the ‘Show-Me State’ the 21st state to legalize cannabis. Some projections suggest sales could reach as high as $550 million in the first year, and potentially as high as $800 million – $900 million by the fourth year. (MJBizDaily Staff, 2022) Beginning December 8th, existing cannabis companies can start applying to switch their business to adult-use. The applications must be reviewed and responded to within sixty days of submission in accordance with legislation. In short, Missouri could log their first adult-use marijuana sales as early as February of 2023.
Before any state can start selling the product to the public, they have to build a regulated market. Sometimes, creating these regulations can take years for states to agree upon; sometimes, it will only take a few months. The deciding factor is dependent upon how motivated the state is to begin receiving tax revenue from legal sales.
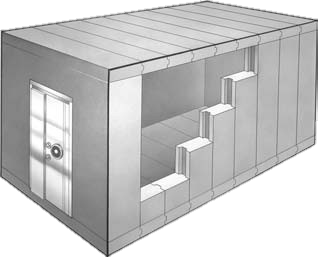
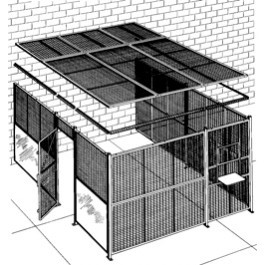
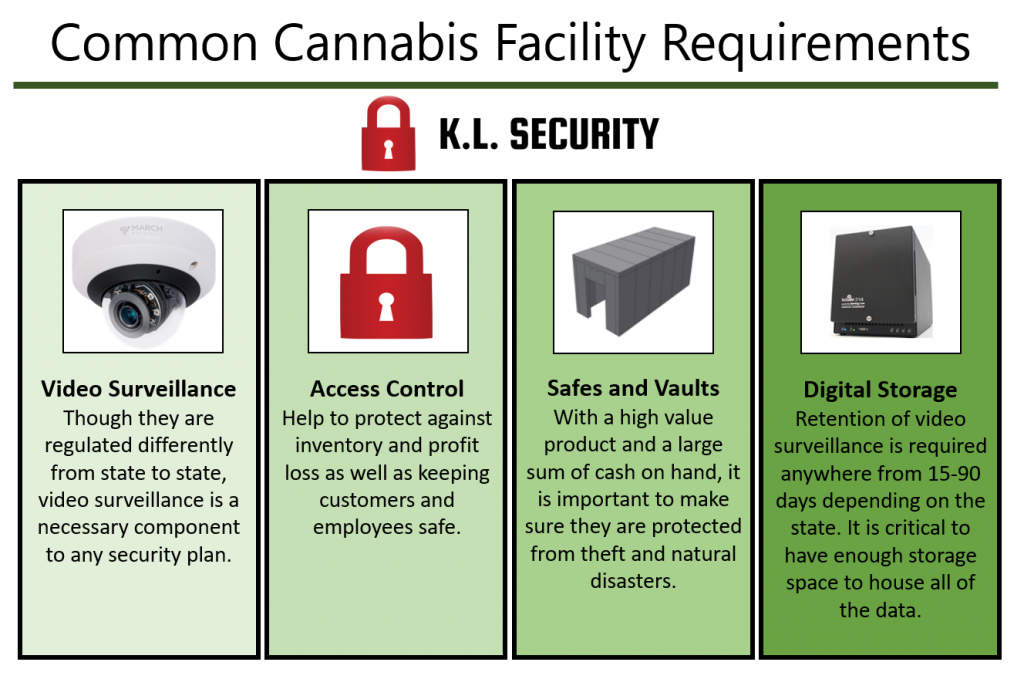
One of the highest priority items for any cannabis operator to consider is ‘how to secure an establishment. Every state requires the creation, adaptation, installation, and maintenance of a security plan: protecting staff & customers as well as securing product & cash are of the utmost importance.
A security plan should:
- Detect, delay, and deter burglaries
- Protect employees, customers, product, equipment, and cash
- Protect against natural disasters
- Deter against theft of cash and product
- Prevent internal diversion
- Be scalable – able to expand with the business
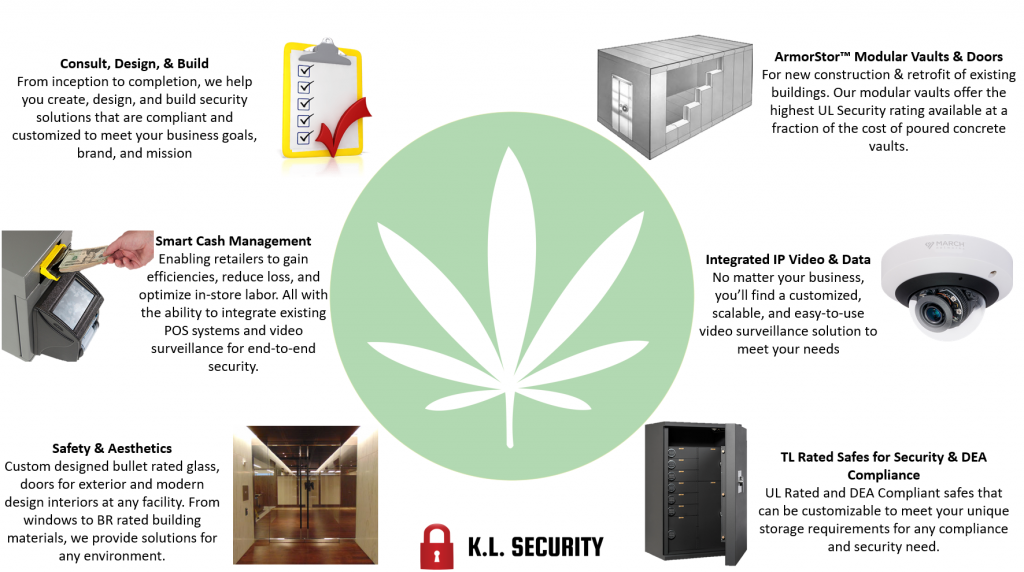
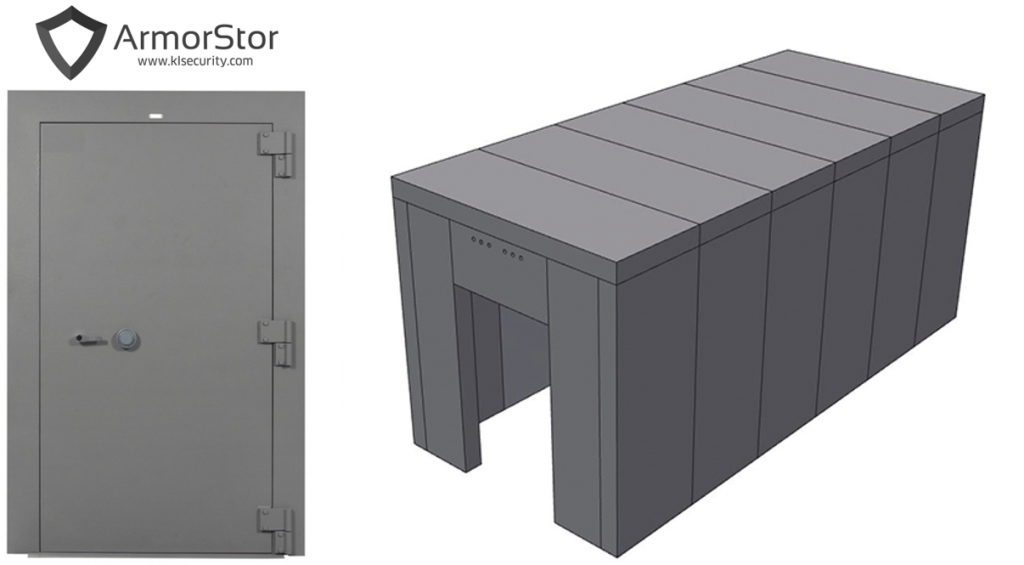
We offer many solutions to help safeguard an operation from potential loss of assets: Bullet rated glass, modular vaults and doors, DEA compliant safes and cages, cash management systems, just to name a few.
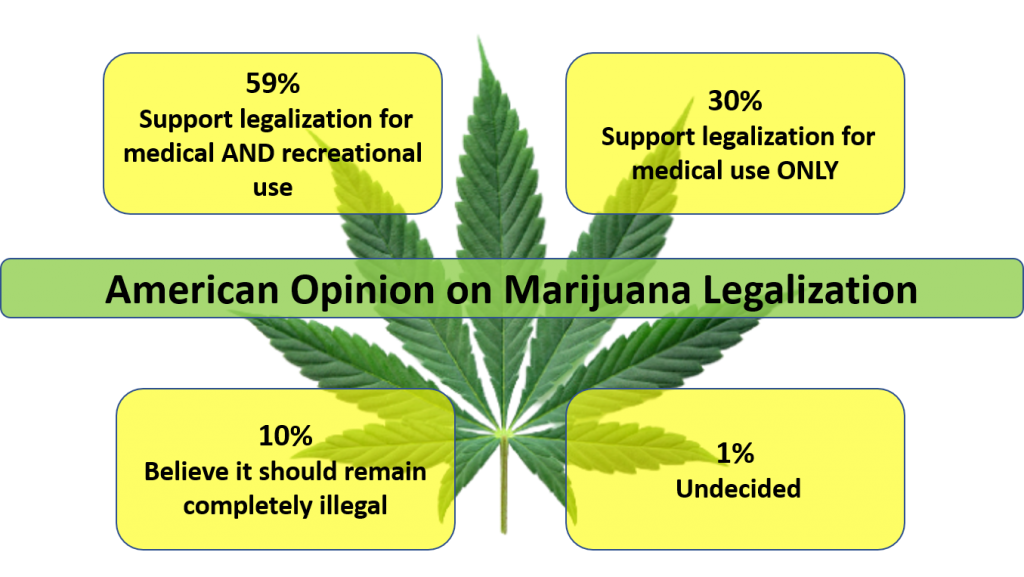
The legalization of marijuana is widely gaining momentum across the country. The majority of Americans are in agreement. According to a study done by Pew Research Center in October, 88% of Americans believe that marijuana should be legal for medical and recreational use by adults (59%) or that it should be legal for medical use only (30%). (GREEN, 2022) This means that only 1 in 10 Americans believe marijuana should remain illegal.
Now is the opportune time to assemble your security plan. Let our experts help you. KL Security focuses on facility security – vaults, cages, cash management safes, high security safes, etc.
Sources:
https://mjbizdaily.com/rhode-island-set-to-launch-recreational-cannabis-market-thursday-dec-1/
https://www.marijuanamoment.net/maryland-voters-approve-marijuana-legalization-referendum-on-ballot/
https://mjbizdaily.com/missouri-could-begin-recreational-marijuana-sales-by-early-february/
https://mjbizdaily.com/us-marijuana-election-wins-maryland-missouri-but-losses-